Donations Make us online
Getty Images
Widely regarded as one of the Internet’s top threats, the Emotet botnet has returned after a months-long hiatus—and it has some new tricks.
Last week, Emotet appeared for the first time this year after a four-month hiatus. It returned with its trademark activity—a wave of malicious spam messages that appear to come from a known contact, address the recipient by name, and seem to be replying to an existing email thread. When Emotet has returned from previous breaks, it has brought new techniques designed to evade endpoint security products and to trick users into clicking on links or enabling dangerous macros in attached Microsoft Office documents. Last week’s resumption of activity was no different.
A malicious email sent last Tuesday, for instance, attached a Word document that had a massive amount of extraneous data added to the end. As a result, the file was more than 500MB in size, big enough to prevent some security products from being able to scan the contents. This technique, known as binary padding or file pumping, works by adding zeros to the end of the document. In the event someone is tricked into enabling the macro, the malicious Windows DLL file that’s delivered is also pumped, causing it to mushroom from 616kB to 548.1MB, researchers from security firm Trend Micro said on Monday.
Another evasion trick spotted in the attached document: excerpts from the Herman Melville classic novel Moby Dick, which appear in a white font over a white page so the text isn’t readable. Some security products automatically flag Microsoft Office files containing just a macro and an image. The invisible text is designed to evade such software while not arousing the suspicion of the target.
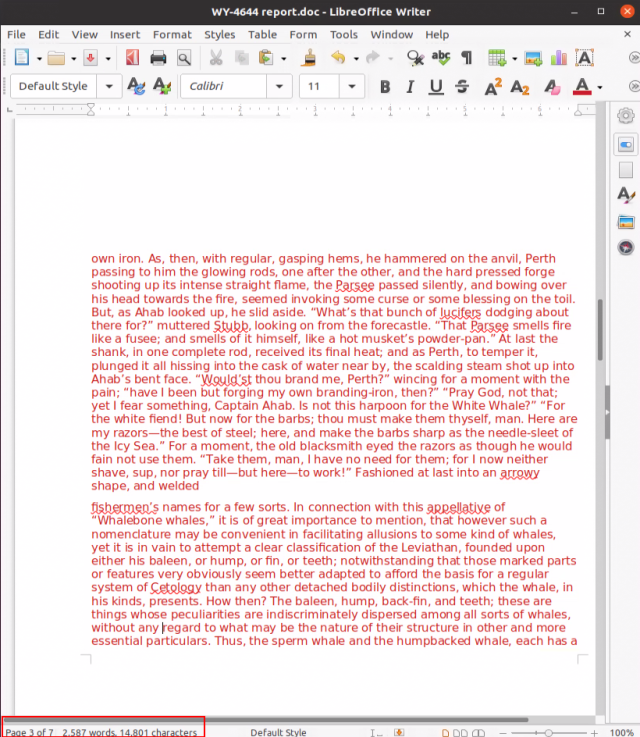
Deep Instinct
When opened, the Word documents present a graphic that says the content can’t be accessed unless the user clicks the “enable content” button. Last year, Microsoft began disabling macros downloaded from the Internet by default.
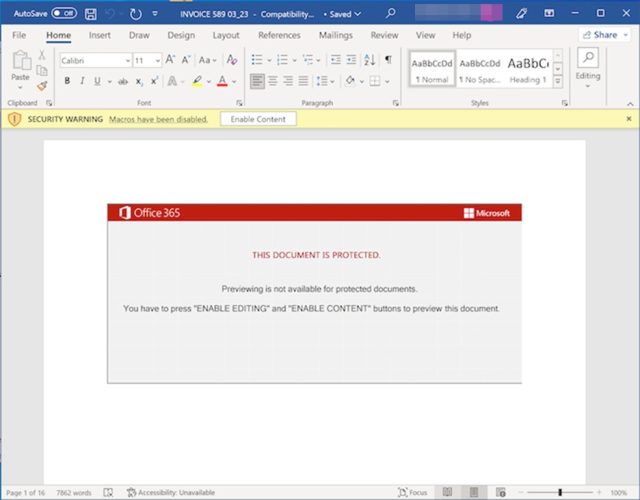
Trend Micro
Clicking the “enable content” button undoes that default and allows the macro to run. The macro causes Office to download a .zip file from a legitimate website that has been hacked. Office will then unzip the archive file and execute the inflated Emotet DLL that infects the device.
Once it has infected a victim’s device, the malware pilfers passwords and other sensitive data and uses the device to send malicious spam to other users. The malware can also download additional malware such as the Ryuk ransomware or the TrickBot malware. The infection chain looks like this:
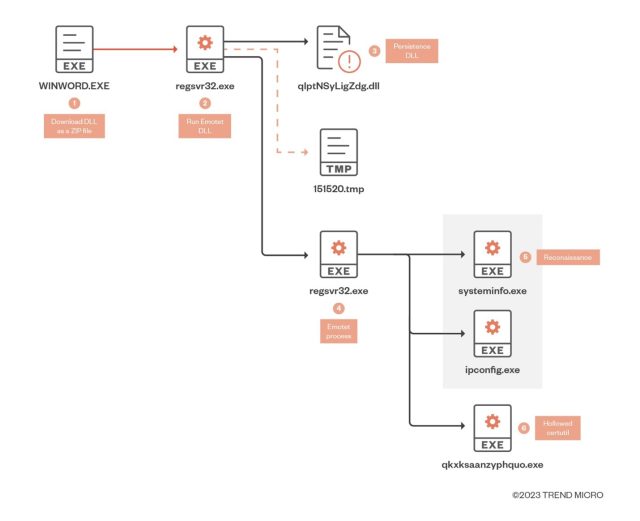
Trend Micro
The attention to detail seen in this latest revival is signature Emotet behavior. For years, the botnet has painstakingly copied received email conversations from infected machines and embedded them into malicious spam sent to other parties in the thread. By following up on an email from someone the target has communicated with in the past, the malicious spam message stands a better chance of going undetected. Emotet can also gain access to Wi-Fi networks and infect connected devices.
With the return of Emotet, people should be on the lookout for malicious emails, even if they appear to come from trusted sources, call the target by name, and include previously sent and received emails. There is rarely a good reason for enabling macros in documents sent by email. People should refuse to allow them to run without first communicating with the sender by phone, instant message, or another non-email medium.
Countries hit the hardest in the latest Emotet run are European, Asian Pacific, and Latin American.
Source link







Leave a Reply