Donations Make us online
Chipmaker TSMC said on Friday that one of its hardware suppliers experienced a “security incident” that allowed the attackers to obtain configurations and settings for some of the servers the company uses in its corporate network. The disclosure came a day after the LockBit ransomware crime syndicate listed TSMC on its extortion site and threatened to publish the data unless it received a payment of $70 million.
The hardware supplier, Kinmax Technology, confirmed that one of its test environments had been attacked by an external group, which was then able to retrieve configuration files and other parameter information. The company said it learned of the breach on Thursday and immediately shut down the compromised systems and notified the affected customer.
“Since the above information has nothing to do with the actual application of the customer, it is only the basic setting at the time of shipment,” Kinmax officials wrote. “At present, no damage has been caused to the customer, and the customer has not been hacked by it.”
In an email, a TSMC representative wrote, “Upon review, this incident has not affected TSMC’s business operations, nor did it compromise any TSMC’s customer information. After the incident, TSMC has immediately terminated its data exchange with this supplier in accordance with the Company’s security protocols and standard operating procedures.” The statement didn’t say if TSMC has been contacted by the attackers or if it plans to pay the ransom.
The statements came shortly after LockBit, one of the most active and pernicious ransomware groups, listed TSMC on its dark web site and demanded $70 million in exchange for deleting the data or transferring it to its rightful owner.
“In the case of payment refusal, also will be published points of entry into the network and passwords and logins company,” the post on the LockBit site said, using broken English that’s characteristic of the Russian-speaking group. “All available data will be published!”
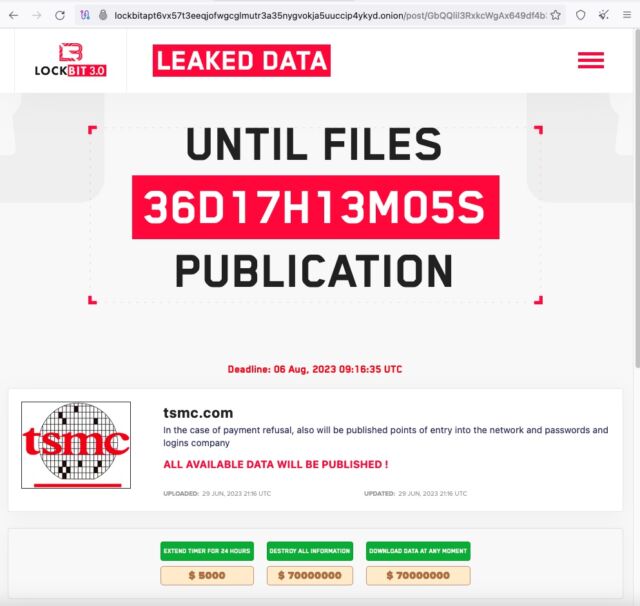
The post included four documents that were allegedly part of the data LockBit obtained. The documents, which included an email, brochure, and what looked like configuration settings, made only oblique references to TSMC and, at first glance, appeared to include no sensitive information.
Like many of the ransomware groups in existence, LockBit operates under a ransomware-as-a-service business model, in which the developers of the LockBit malware lease it to affiliates. The affiliates attempt to breach the networks of organizations and, when successful, use the LockBit ransomware to encrypt data. If the victim pays a ransom, the affiliates share a portion with the developers.
LockBit was first observed in 2019 and has gone through several transitions. It was referred to as ABCD, a reference to the extension appended to files it encrypted. Later, the extension changed to LockBit. Last June, the developers released LockBit 2.0 as part of an advertising campaign aimed at recruiting new affiliates. The group has successfully extorted $91 million since 2020, the Cybersecurity and Information Security Agency said recently. As of July 2021, there were 9,955 submissions to ID Ransomware, an online tool that helps the ransomware victims identify which ransomware has encrypted their files. Security firm Emsisoft has more about LockBit here.
TSMC said that every hardware component installed in its network must first undergo “extensive checks and adjustments” that include security configurations. The breach remains under an investigation that involves a law enforcement agency, the chipmaker said.
Kinmax offered “sincere apologies to the affected customers.” Use of the plural suggested TSMC wasn’t the only Kinmax customer to have data stolen in the breach. Kinmax didn’t elaborate. Earlier on Friday, the Kinmax website listed partners, including companies HPE, Aruba, Cisco, Microsoft, Citrix, Red Hat, and VMware. The site removed those references shortly before this post went live on Ars.
The Kinmax breach comes two weeks after the US Justice Department announced it had arrested Ruslan Magomedovich Astamirov (АСТАМИРОВ, Руслан Магомедовичь), a 20-year-old Russian national, for his alleged participation in several LockBit ransomware attacks in the US and elsewhere. One day earlier, the LockBit site claimed it hacked Indian pharmaceutical company Granules India and published a large trove of documents the group said it had obtained.
Source link






Leave a Reply