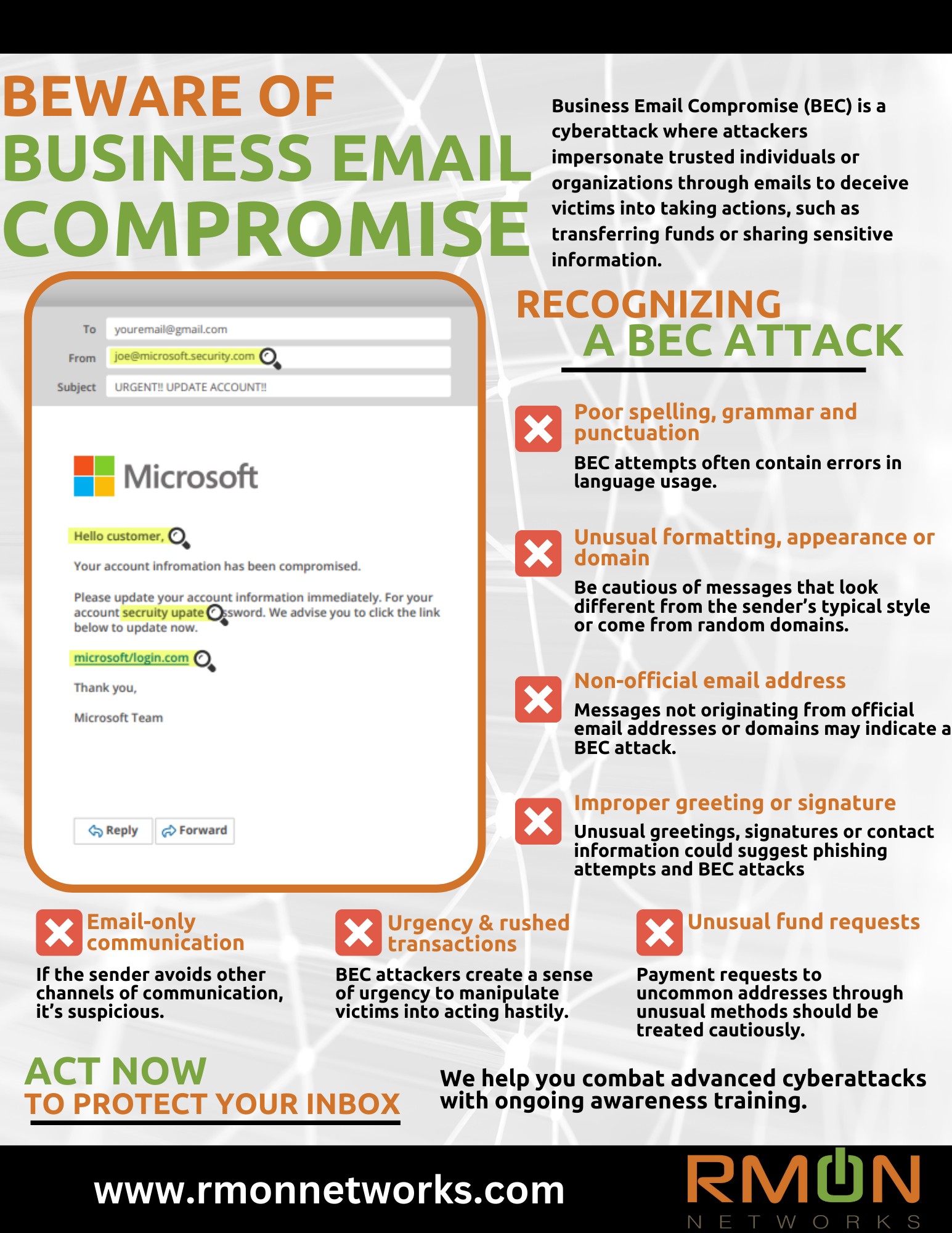
Download our infographic to protect your business from costly cybercrime. Business email compromise (BEC) is a phishing attack deployed by cybercriminals to trick employees into transferring funds or sharing sensitive information. BEC scams are cleverly crafted to convince the receiver ...
Download our checklist to build a resilient cybersecurity culture in your organization. Solely investing your time and resources in technology won’t protect your business from cybercriminals. You also need the help of a trained workforce. If you want your employees ...
The term “use by date” is commonly associated with food and medication as it indicates the date after which these products are no longer safe to consume. However, it’s important to note that hardware and software can also expire. Technology ...
Find out more on how an outsourced IT provider can guide you to success. Are you finding it difficult to keep up with the ever-changing technology landscape? Managing your IT needs in-house can be expensive and challenging. But there’s a ...
As technology continues to advance at an ever-increasing pace, businesses face mounting demands on their IT infrastructure. To address these challenges effectively, outsourcing your IT needs to a third-party provider is becoming the go-to option. By partnering with experts in ...