Our daily lives have become increasingly dependent on mobile apps, whether it’s for shopping, ordering food, or managing our finances. However, their associated risks have also been raised with the increasing use of mobile apps. Mobile app security is essential for developers, businesses, and users.
According to the latest report published by Symantec, there was a 54% uprise in mobile malware variants in 2017 alone, with 27.4 million new samples discovered. It shows that mobile app security is a serious issue that needs to be resolved. In this blog, we will find some of the best strategies for mobile app security and the common vulnerabilities that app developers should be mindful of.
By following the best approach and understanding common vulnerabilities, app developers can ensure that their mobile apps are secure and that users’ sensitive data is shielded. It is essential for businesses and users also to be conscious of these security threats and take the needed safeguards to protect themselves.
This blog will delve more in-depth into the mobile app security world, providing insights and tips on developing secure apps and avoiding common exposures.
What is Mobile App Security?
Mobile app security guides the measures to save mobile applications from unauthorized access, damage, or theft. With the increasing use of smartphones and mobile devices, mobile app security has become a critical issue for users and businesses. Mobile app security concerns enforcing various security protocols and features to guarantee the application has been fixed, and user data is protected.
It possesses secure data encryption, user authentication, coding practices, access controls, and more. Mobile apps are vulnerable to cyberattacks, such as identity theft, data breaches, and more, without appropriate security steps. Therefore, mobile app developers need to prioritize security and implement the best techniques to protect user data and confirm the safety of their applications.
Best Practices for Securing Mobile Apps
With the growth in mobile app usage, the security of these mobile apps has become a significant problem. Cyberpunks are always looking for vulnerabilities to manipulate, and any security loophole can lead to a data breach, which can have severe consequences. Therefore, following the best methods for securing mobile apps is crucial.
Here we will discuss 10 best practices that can authorize secure mobile apps
1. Secure Code:
The first and superior best method for securing mobile apps is to write secure code. Following the best coding practices and guidelines guarantees the code is safe. The code should be cross-checked daily, and any vulnerabilities need to be improved immediately.
Benefits of Secure Code
✅ Protects user data: Secure code ensures that sensitive user data, such as login credentials, personal information, and financial data, is protected from unauthorized access, theft, and misuse.
✅ Prevents data breaches: By incorporating secure coding practices, mobile app developers can prevent common vulnerabilities, such as SQL injections, cross-site scripting (XSS), and buffer overflows, which hackers can exploit to gain unauthorized access to user data.
✅ Maintains app reputation: Apps compromised due to security vulnerabilities can lead to a loss of user trust and a damaged reputation. Secure code helps to maintain the integrity and importance of the app.
✅ Compliance with regulations: Many industries, such as healthcare and finance, have specific rules for protecting user data. By implementing secure code, mobile apps can ensure compliance with these regulations.
✅ Cost-effective: Fixing security vulnerabilities after an app has been released can be costly and time-consuming. By incorporating secure code as part of the development process, mobile app developers can save time and money in the long run.
2. Use Encryption:
Encryption is transforming data into a code to control unauthorized access. Encrypt approaches to secure sensitive data such as user payment details, credentials, and personal information are essential.

Benefits of Encryption
✅ Protects sensitive data: Encryption is an effective method to protect sensitive data, such as financial data, personal information, login credentials, and other sensitive information stored on mobile apps. Encrypting data prevents unauthorized access, ensuring that confidential information remains secure.
✅ Prevents data breaches: Data breaches can be disastrous for mobile apps and their users, as they can lead to the loss of sensitive information, financial loss, and reputational damage. Encryption can help prevent data breaches by making it harder for attackers to read the data they have stolen, thus reducing the chances of a successful data breach.
✅ Complies with regulations: Many industries and countries have laws that mandate using Ciphered to protect sensitive data. Organizations can comply with these regulations by implementing Concealing in mobile apps and avoid costly fines and penalties.
✅ Builds trust with users: Users expect their personal information to be kept secure, and they may only trust mobile apps with adequate security measures. Using encryption as a best practice, mobile apps can build trust with their users and demonstrate a commitment to protecting their data.
✅ Provides a competitive advantage: Mobile apps with robust security measures, such as encoding, may have a competitive advantage over those that do not. Mobile apps can attract and retain users who prioritize security and privacy by demonstrating a commitment to safety.
3. User Authentication:
User authentication is the method of verifying the identity of the user. Robust user authentication mechanisms are necessary to prevent unauthorized access to the mobile app. Multi-factor authentication can be used to boost the security of the mobile app.
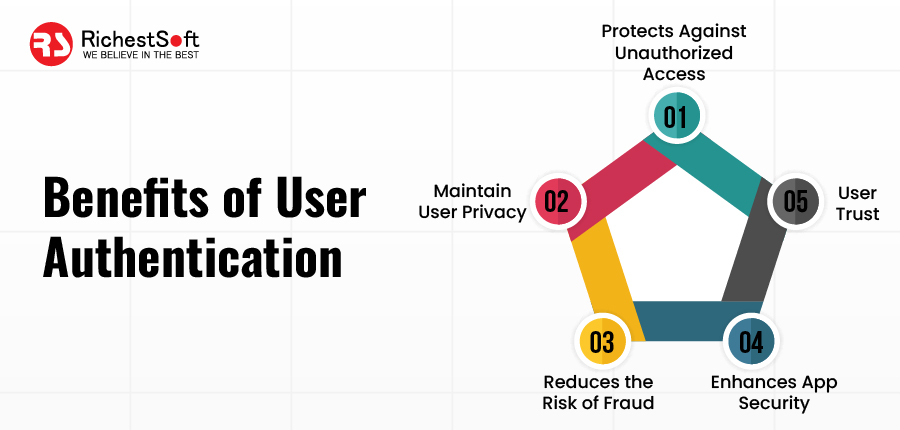
Benefits of User Authentication
✅ Protects against unauthorized access: User authentication is an effective way to protect against unauthorized access to the app’s data and functionality. Requiring users to log in with a unique username and password ensures that only authorized users can access the app’s features and data.
✅ Helps maintain user privacy: User authentication can also help preserve user privacy by ensuring that only the intended user can access their data. It is important for apps that store sensitive information, such as financial data or health records.
✅ Reduces the risk of fraud: User authentication can help to reduce the risk of fraud by ensuring that users are who they claim to be. It is salient for apps that involve financial transactions or sensitive data.
✅ Enhances app security: User authentication can be combined with other security measures to improve overall app security. For example, it can be used with encryption and secure coding practices to provide multiple layers of protection against potential threats.
✅ Builds user trust: By implementing user authentication as a best practice, app developers can help to build user trust by demonstrating a commitment to protecting user privacy and data. It leads to increased user engagement and loyalty.
4. Data Minimization:
Data minimization is the method of collecting and storing only the necessary data. Storing unnecessary data raises the risk of data breaches. Therefore, it is crucial to collect and store only the needed data.
Benefits of Data Minimization
✅ Reduced Risk of Data Breaches: The risk of data breaches is significantly reduced by minimizing the amount of sensitive data stored on the app and its servers. It is because hackers can steal less data, decreasing the likelihood of a successful cyber attack.
✅ Compliance with Regulations: Data minimization is recommended by GDPR, HIPAA, and CCPA. By following this best practice, mobile app developers can ensure their app complies with these regulations and avoid legal penalties.
✅ Improved User Privacy: Users are becoming more conscious about their privacy and are increasingly hesitant to share their personal information with mobile apps. By implementing data minimization, app developers can assure users that their data is being collected only when necessary and that it is not being stored longer than needed.
✅ Reduced Costs: By storing fewer data, app developers can reduce the cost of storing and securing data. It is beneficial for smaller companies needing more resources to invest in extensive security measures.
✅ Improved App Performance: Mobile apps that store large amounts of data can experience performance issues. By minimizing the amount of data stored, developers can improve the app’s performance and reduce load times, resulting in a better user experience.
5. Regular Updates:
Regular updates can help fix security vulnerabilities and improve the app’s security. It is essential to update the mobile app regularly to guarantee that it is protected and free from vulnerabilities.
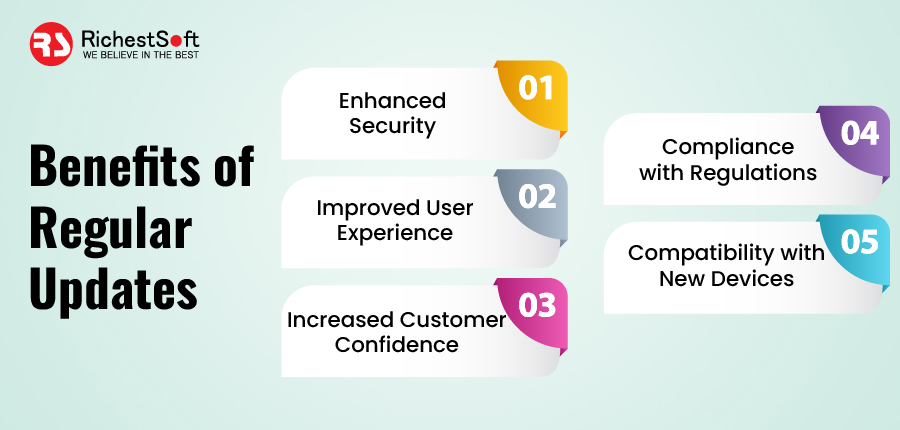
Benefits of Regular Updates
✅ Enhanced Security: Regular updates can help address security vulnerabilities and fix bugs that attackers could exploit. By staying up-to-date with the latest security patches, you can significantly decrease the risk of a cyber attack on your app.
✅ Improved User Experience: Updating your app regularly can improve its functionality and user experience. New features and bug fixes can enhance the app’s performance, making it more efficient and user-friendly.
✅ Increased Customer Confidence: Regular updates demonstrate your commitment to your users’ security and privacy. It can boost customer confidence, help retain existing users, and attract new ones.
✅ Compliance with Regulations: Mobile apps that handle sensitive data, such as financial or health information, may be subject to regulatory requirements for data protection. Regular updates help ensure compliance with these regulations and reduce the risk of costly fines and legal action.
✅ Compatibility with New Devices and Operating Systems: New devices and operating systems are constantly being released, and regular updates help ensure your app is compatible with these new technologies. It can expand your app’s potential user base and keep it relevant in a rapidly changing mobile landscape.
6. Use of SSL/TLS:
SSL/TLS is a security protocol that encrypts the data exchanged between the customer and the server. It is crucial to use SSL/TLS to guarantee that the data exchanged between the mobile app and the server is secure.
Benefits of SSL/TLS
✅ Data privacy: SSL/TLS provides end-to-end Encryption, ensuring that the data transmitted between the app and server is secure and private. It is foremost when sensitive information – personal, financial, and health records are involved.
✅ Prevents Man-in-the-middle attacks: SSL/TLS protocol helps prevent man-in-the-middle attacks that may occur when an attacker intercepts and manipulates data transmitted between the app and server. It can be done by verifying the essence of the server, thereby establishing a secure connection.
✅ Ensures the authenticity of data: SSL/TLS ensures that data is transmitted without being altered or tampered with during transmission. It is accomplished by using digital signatures that demonstrate the authenticity and integrity of the data.
✅ Boosts customer trust: Using SSL/TLS can improve customers’ confidence in an app, knowing that their data is being relayed securely. It is beneficial for financial and e-commerce apps where customers share sensitive information.
✅ Regulatory compliance: Many regulatory frameworks require SSL/TLS, particularly when transmitting sensitive data. Using SSL/TLS, mobile apps can comply with these regulations and avoid potential penalties or legal consequences.
7. Code Obfuscation:
Code obfuscation is the method of making the code complex and challenging to understand. It can help control the reverse engineering of the mobile app, leading to security vulnerabilities.
Benefits of Code Obfuscation
✅ Protection against reverse engineering: Code obfuscation makes it more difficult for attackers to reverse engineer your app’s code and extract sensitive information or create unauthorized copies of your app.
✅ Improved app performance: Code obfuscation can also lead to improved app performance by reducing the size of the code and making it more efficient.
✅ Enhanced security of encryption keys and algorithms: By obfuscating code that contains sensitive information, such as encryption keys and algorithms, you can further protect these elements from being discovered and exploited by attackers.
✅ Minimizing the impact of app vulnerabilities: Obfuscating code can make it more difficult for attackers to exploit vulnerabilities in your app’s code, reducing the effects of any security breaches.
✅ Meeting regulatory and compliance requirements: Many industries, such as finance and healthcare, have strict regulatory requirements regarding the security of mobile apps. Using code obfuscation as a best practice can help ensure compliance with these regulations and avoid costly fines or legal issues.
8. Use of Security Libraries:
There are several security libraries available that can be used to boost the security of the mobile app. These libraries deliver various security features like authentication, Encryption, and data validation.
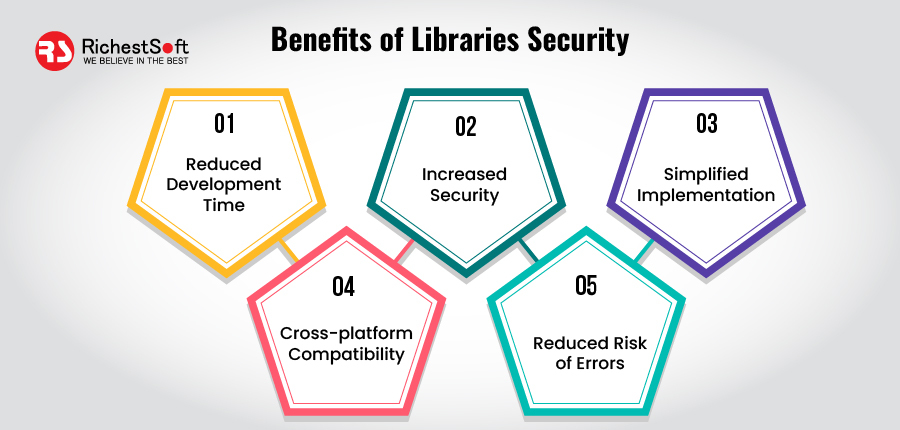
Benefits of Security for Libraries
✅ Reduced development time: Security libraries provide pre-built code modules that can be integrated into the app’s source code, saving development time and effort. Developers can easily add data encryption, authentication, and secure network communication without writing custom code.
✅ Increased security: Security experts build certain libraries and are constantly updated to address new security threats. It ensures that the app is a safeguard against known vulnerabilities and current security features.
✅ Simplified implementation: Security libraries are created to be easy to implement, with clear documentation and code samples that can be simply integrated into the app’s source code. It makes it easier for developers to follow best security practices without spending infinite time researching and developing custom solutions.
✅ Cross-platform compatibility: Many security libraries are designed to work across multiple platforms, such as Android and iOS, making it easier for developers to ensure their app is secure across all devices and operating systems.
✅ Reduced risk of errors: Using pre-built security libraries minimizes the risk of introducing errors or vulnerabilities into the app’s source code. It is because security experts have tested and validated the libraries and are less likely to contain mistakes or flaws than in-house custom code.
9. Penetration Testing:
Penetration testing tests the mobile app for vulnerabilities by simulating a real-world attack. It can assist in identifying security vulnerabilities that may have been overlooked during development.

Benefits of Penetration Testing
Identify vulnerabilities: Penetration testing helps to identify potential security vulnerabilities in mobile applications before attackers can exploit them. It allows developers to address these vulnerabilities before deploying the application to users.
✅ Validate security controls: Penetration testing can validate the effectiveness of security controls and measures in place. It ensures that the security controls work as intended and can prevent unauthorized access or data breaches.
✅ Compliance: Penetration testing is required by regulatory frameworks such as GDPR and PCI DSS. By performing regular penetration testing, organizations can demonstrate compliance with these regulations and standards.
✅ Continuous improvement: Penetration testing can be used as a continuous improvement tool to enhance the security of mobile applications. The insights and feedback obtained from testing can be used to improve the application’s security.
✅ Protect brand reputation: A security breach or vulnerability in a mobile application can severely impact an organization’s brand reputation. By incorporating penetration testing as a best practice, organizations can prevent such incidents from happening and protect their brand reputation.
10. App Permissions:
App permissions are the permissions the mobile app requests to access the device’s resources. It is essential to guarantee that the app requests only the necessary permissions. Requesting unnecessary permissions can lead to security vulnerabilities.

Benefits of App Permissions
✅ Increased User Trust: By using app permissions, you can ensure that your app only accesses the information it needs to function correctly. It can improve user trust in your app and help to build a positive reputation.
✅ Better User Experience: App permissions can provide a better user experience by only requesting necessary information and reducing the number of permission requests. It can also help to prevent user frustration and abandonment of the app.
✅ Reduced Security Risks: Properly managing app permissions can decrease the risk of security breaches and protect sensitive information from unauthorized access. It can help to safeguard user data and maintain the integrity of your app.
✅ Compliance with Regulations: Many countries and industries have specific regulations regarding collecting and using personal data. By implementing app permissions, you can ensure that your app complies with these regulations and avoid potential legal issues.
✅ Improved App Performance: By minimizing the amount of data your app collects and the number of permission requests, you can improve app performance and reduce the amount of memory and processing power your app requires. It can lead to faster load times and improved overall user experience.
Tools & Technologies to Secure Mobile Apps
Mobile app security is critical for app developers, businesses, and end-users. Fortunately, various tools and technologies are available to secure mobile apps and minimize the risk of vulnerabilities and data breaches. Here are some of the most famous tools and technologies to strengthen mobile apps:
- Mobile Device Management (MDM) solutions to manage and secure devices remotely.
- Mobile app security testing tools like OWASP Mobile and Veracode detect vulnerabilities in mobile apps.
- Multi-Factor Authentication (MFA) adds an extra layer of security and decreases the risk of unauthorized access.
- Encryption technologies like SSL/TLS, AES, and RSA to secure data in transit.
- App shielding and hardening techniques like code obfuscation, app wrapping, and runtime application self-protection (RASP) protect mobile apps from reverse engineering and tampering.
- App analytics and monitoring tools like Google Analytics and Firebase utilize to track user behavior and detect anomalies.
- Secure coding frameworks like React Native and Xamarin to develop fortified and reliable mobile apps.
FAQs
Q1: What are some common vulnerabilities in mobile apps?
Ans: Some common vulnerabilities in mobile apps include code injection, insecure data storage, weak or insecure authentication, data leakage, and insufficient encryption.
Q2: What are some best practices for mobile app security?
Ans: Best techniques for mobile app security include executing secure code practices, minimizing data storage, using encryption, implementing user authentication, and using SSL/TLS.
Q3: How can I ensure that my mobile app is secure?
Ans: You can confirm your mobile app is secure by conducting regular security audits, implementing security measures during development, and penetration testing, staying updated with the latest security trends and patches, and educating your mobile users on safe app usage patterns.
Q4: What should I do if I find a vulnerability in my mobile app?
Ans: If you find a susceptibility in your mobile app, you should instantly patch the vulnerability and notify your users of the issue. You should also conduct a thorough investigation to resolve how the vulnerability was introduced and take security measures to prevent similar problems from occurring.
Conclusion
Mobile app security is an essential and complex element of the mobile app development approach. With mobile devices being used for more sensitive data than ever, learning best practices and common vulnerabilities associated with mobile apps has become even more critical. By understanding these ideas and taking the proper steps, such as blacklisting untrusted sources, using secure coding techniques, and deploying a complete security testing method, you can develop robust mobile apps that safeguard your users’ data from malicious actors.






Leave a Reply